
In this post I will go through the vocabulary around the wireless technologies. I will also show tools you can use to test in your own environment.
This post is part of a series called “Ethical Hacking”.

During the CEH v10 certification you will get to know a lot of tools that helps you with the 5 phases of a hack.
One of the most valuable tools out there is Metasploit.
The Metasploit Project is a computer security project that provides information about security vulnerabilities and aids in penetration testing and IDS signature development. Its best-known sub-project is the open source Metasploit Framework, a tool for developing and executing exploit code against a remote target machine. Other important sub-projects include the Opcode Database, shellcode archive and related research. The Metasploit Project is well known for its anti-forensic and evasion tools, some of which are built into the Metasploit Framework.
I will go through some of ways you can use Metasploit to your advantage.
This post is part of a series called “Ethical Hacking”.

In this article, I will go in depth with 3 scanners you can use. The scanners are Nmap, Scruby and Hping3. You can use these scanners to see what ports are open/closed, which OS, banner grabbing and a lot more.
This post is part of a series called “Ethical Hacking”.
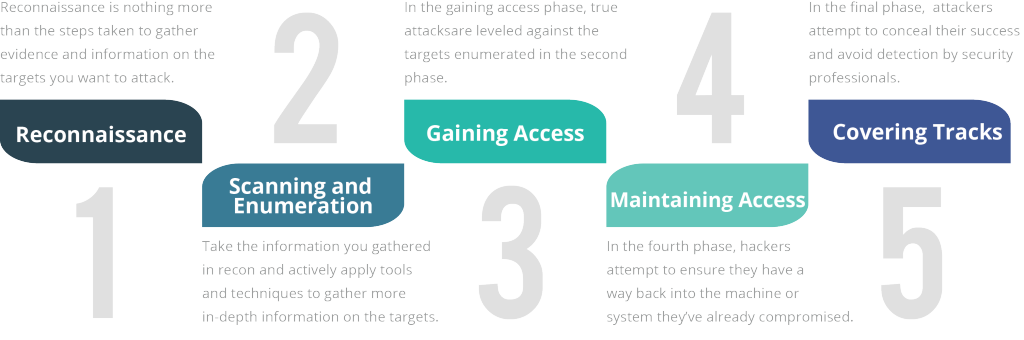
After finishing two MCSA (Office 365 & Windows Server 2012 R2) certifications, I’m currently studying to take the CEH v10 certification, which is a valuable tool for any IT-professional.
This post is part of a series called “Ethical Hacking”.
While I’m studying for this certification, I’m going to update this post with variety of useful tools and websites. Only use these tools in your own environment for education purposes only.